Many have already written about the cybersecurity vulnerability of our educational institutions and the urgent need to improve, including the recent "This Magic Moment: Reflections on Cybersecurity" by Kim Milford and Joanna Grama. We need a risk management approach to cybersecurity and cannot rely on annual cybersecurity program audits to effect a real change in cybersecurity posture. Instead, measurement of our cybersecurity risk posture would enable informed business decisions.
What Is at Risk?
As identified in Milford and Grama, table 1, organizations must overcome the "I'm not a target" mentality. Every educational institution is a rich target for someone:
- They create the nation's intellectual capital and cutting-edge research.
- The distributed IT model (college, department, program, etc.) is more vulnerable to persistent attack.
- Their powerful computing infrastructure can be used in attacking someone else.
- They store payment and identity information, including:
- Students near the beginning of their financial profiles
- Parents' financial information
- Alumni and donors with substantial assets
- Personnel involved with topics of interest to attackers
- Openness makes the environment more difficult to secure.
- Open academic environment, with sharing and collaboration by purpose
- Multiple personas and legacy access
- Open doors to the community
Why does cybersecurity matter? If the protection of our nation's intellectual capital, which shapes the foundation for our technical and economic future, is not reason enough, then maybe the protection of our faculty, staff, and students' economic future from identity theft, or not having our resources used to compromise someone else, might provide sufficient reason. In addition, we should consider protecting our institutions' most valuable and precious resource: their reputations.
The reputation of the educational institution is fundamental to its long-term success. Good reputation drives high-quality student demand, significant research opportunities, high-quality faculty and staff, alumni good will, and everything else.
How Can We Improve?
We know that cybersecurity is difficult to achieve, and no one has enough resources to protect everything at the same level. We also know that no matter how much we spend, no matter how hard we try, no matter how effective our security controls, we always have the chance of being breached. The most beneficial strategy to apply in this kind of environment is a risk management approach.
A risk management approach to cybersecurity enables the organization to prioritize all aspects of its cybersecurity program, as part of its existing enterprise risk management (ERM) program. The NIST Cybersecurity Framework (NIST CSF) was developed to enable those responsible for ERM decisions to gain insight into their cybersecurity risks. Despite some confusion about the intended role for the NIST CSF, it is not meant to replace cybersecurity technical standards (policies, procedures, and controls) such as NIST 800-53, COBIT5, ISO 27001, etc. The NIST CSF established a common language and structure enabling the discussion of cybersecurity best practices among various industries, organizations, and groups, and within the organization itself. It aims to bridge the communication gap between the technical and business domains so that cybersecurity risk can be incorporated into ERM.
The NIST CSF process may be summarized with the following three questions:
- What are your organization's critical assets?
- What are the likely high-impact threats?
- What is your strategy to protect your assets from those threats (i.e., what are you willing to do)?
Forming a prioritized strategy (where strategy = actions taken to achieve an aim) is a good start, but not sufficient to achieve a verifiable cybersecurity defense posture. What truly matters is the organization's ability to execute the strategy well and measure it:
- How do you prioritize your day-to-day response and actions?
- How to you link your efforts to your risk-mitigation strategy?
- How do you measure your organization's response?
- How do you measure the effectiveness of the results of its activities?
- How do you measure the cybersecurity risk in your supply chain risk (product and service providers)?
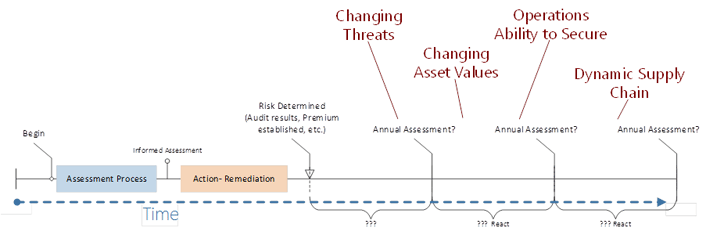
Annual Audits Are Not Effective Enough
The typical approach to cybersecurity risk management is an annual assessment, either a self-assessment or a third-party audit of the organization's cybersecurity program. The news is filled with reports of companies that were in a state of compliance with their security program but had a massive data breach event anyway. The most common reason? We live in a dynamic environment, and an audit represents a point-in-time, sample of evidence, assessment. Breach root-cause analysis typically reveals indicators of system compromise to which the organization has made no response. Most organizations begin their breach response when notified by a third party that their data has been stolen or their systems are being used by someone else. In general, this typically represents ineffective execution of the activities the organization has identified for the protection of its critical assets, according to its desired cybersecurity risk management goals.
New Approach
The NIST CSF enables a way to effect consistent prioritization, execution, and measurement of the organization's activity to produce the outcomes needed to achieve its desired cybersecurity risk-management goals, tailored to each institution. This new approach resembles continuous process control for cybersecurity, with process control defined as "Activities involved in ensuring a process is predictable, stable, and consistently operating at the target level of performance with only normal variation."
Industry has begun to produce frameworks and systems for measuring their cybersecurity risk posture based on operationalizing the NIST CSF, but only wide adoption will bring it to maturity. I encourage educational institutions to adopt the NIST CSF risk management approach and to consider the use and refinement of cybersecurity risk posture measurement to lead our nation in protecting its future.
David Leigh is a co-founder of Rofori Corporation, which produces DEFCON CYBER software. Prior to this he was senior consultant and vice president of NetBase Corporation Solutions Services and program manager for the Department of Labor Administrative Law Judges Case Management System, as well as the Farm Service Agency Credit Commodity Corporation. Leigh has over 24 years of experience in the definition, development management, and implementation of decision support systems. During his time at McDonnell Douglas, cybersecurity and resiliency were paramount requirements for his commercial aircraft program manufacturing process control systems integration efforts. Leigh holds a BS in Mechanical Engineering and an MS in Industrial Engineering and Management from Oklahoma State University.
© 2015 David Leigh. This EDUCAUSE Review blog is licensed under the Creative Commons BY-NC-SA 4.0 International license.
