Did you know that over 70 percent of security awareness officers spend less than 25 percent of their time on security awareness (figure 1)?1 That means the vast majority of us run an awareness program while also held responsible for numerous other projects. We could spend hours discussing how misguided leadership underfunds such a key effort, but not today. Instead, let's focus on how we can have an impact with the time and resources available. In this blog I wanted to share with you how organizations successfully deploy awareness programs while facing similar challenges.
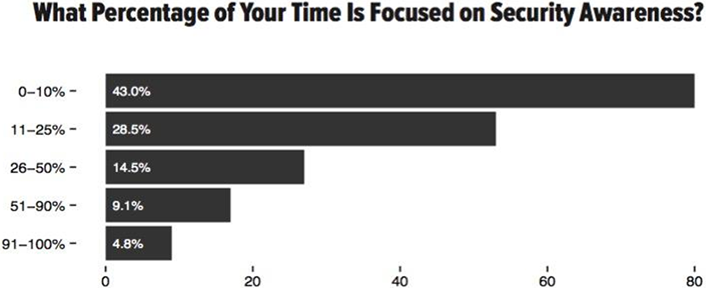
Figure 1. Time security awareness officers spend on security awareness
Step 1: Prioritize
First and foremost, you can't do everything yourself. You will not be able to save the world or mitigate all the human risks in your organization. So the first thing you need to do is prioritize. Identify the top human risks to your organization and focus on those. This may be as simple as going to your incident response team and asking them what they see as the top human incidents occurring. Or it might require a more formal human-risk analysis of your entire organization or specific departments. Once you identify your top human risks (such as phishing, accidental data loss, poor password practices, etc.), you will then need to identify the secure behaviors people should exhibit in order to manage those risks. The key is prioritizing your human risks and the behaviors that mitigate those risks. Ultimately, the fewer human risks and behaviors you focus on, the more likely you will succeed in changing them. So first things first: reduce your scope to what you can manage and where you will have the biggest impact.
Step 2: Seek Help
Second, ask for help. In almost every organization I have worked with that has a mature awareness program, it has never been a one-person show. Successful awareness programs require a team of different people with different skills. For example, bring in someone from communications to help you communicate your awareness program. In fact, in larger organizations I often find someone from the communications department embedded into the security team. Consider having someone from the audit department help you meet the compliance requirements. Pull someone in from human resources to help you identify your organization's culture and the different target groups and develop ideas about how to engage them. Take these people with different skills and create an advisory board, then leverage this advisory board for help in building, maintaining, and measuring your awareness program. One idea is to even include a senior executive on your board, giving it credibility while also giving you a channel to senior leadership.
The key to making this work is ensuring that they benefit from helping you. The more you can do for them, the more they will do for you. Ideas include:
- E-mail their boss thanking them for their employee's amazing support and highlighting the difference that person made. Perhaps even create a certificate for them to hang on their wall.
- Have the chief information security officer (CISO) or some other senior executive e-mail each of these individuals thanking them (and copy their boss).
- Let each person know they will have an opportunity to meet other people in the organization they wouldn't normally get the chance to meet, allowing them to build their network.
- Give them the opportunity to develop a new skill set (cybersecurity) and learn how to better protect themselves at work and at home.
- Explain how their time and efforts will make a difference to the organization.
Because awareness requires so many different skills and touches so many different people, you cannot succeed operating in a vacuum; you need help from others.
Step 3: Learn from Others
Finally, do not reinvent the wheel. A huge community of security awareness officers out there is developing and sharing resources you can use. Leverage these materials and lessons learned, saving time and making you more productive and your program more effective. Some key resources include:
- Security Awareness Planning Kit: The biggest challenge to creating an effective awareness program is first having a plan. This kit provides a complete framework with all of the templates, charts, and examples you need to hit the ground running.
- Phishing Assessment Planning Kit [http://www.securingthehuman.org/media/resources/PhishingPlanningKit.zip]: The biggest challenge with any phishing program is not the technology you choose but how you structure and communicate your program. This kit combines the lessons learned from hundreds of phishing programs.
- OUCH Security Awareness Newsletter: Don't have time to create a monthly security awareness newsletter? OUCH! is for you. Developed by a community of volunteers and translated into 20+ languages, this newsletter can help you communicate your key messages.
- Tip of the Day: A great resource for daily security reminders that you can embed in your own website.
- Awareness Posters: Developed by fellow awareness officers, these posters share key messages. Print and distribute as many as you like.
Make a Difference
You will not be able to save the world, nor will you be able to eliminate every human risk. But regardless of your limited time, taking these three steps helps you make a positive difference in your institution's security awareness and behaviors.
Note
- See the SANS 2015 Security Awareness Report.
Lance Spitzner is director of SANS Securing The Human. He has over 20 years of security experience in cyber threat research, awareness, and training. He invented the concept of honeynets, founded the Honeynet Project, and published three security books. He has worked and presented in over 25 countries and helped more than 350 organizations plan, maintain, and measure their security awareness programs. In addition, he is a serial tweeter (@lspitzner) and avid blogger, and works on numerous community security projects. Before working in information security, Mr. Spitzner served as an armor officer in the Army's Rapid Deployment Force and earned his MBA from the University of Illinois.
© 2015 Lance Spitzner. This EDUCAUSE Review blog is licensed under the Creative Commons BY-NC-SA 4.0 International license.
